LINUX BASICS
Secure the Linux system and its files
The ever-watchful Nick Peers discovers how Linux is built from the ground up to help keep you and your data secure.
Part Seven!
Don’t miss next issue, subscribe on page 16!
OUR EXPERT
Nick Peers has seen his fair share of viruses over the years, but has yet to see any appear on his Linux machine. Talk about tempting fate…
One key advantage of Linux is that it’s been built with security in mind. As earlier versions of Windows practically invited malware on to their insecure systems, Linux’s early developers were taking notes and making sure they didn’t fall into the same trap. As a result, the Linux kernel – the core interface between your PC’s hardware and its own processes – is written with security as a key priority.
In this Linux Basics tutorial, we’re exploring the most notable ways in which Linux is designed to keep everything from your user account to your files safe, snug and secure.
User privileges
One of the most visible ways in which Linux is more secure than the likes of Windows is with its user privilege model. They say imitation is the sincerest form of flattery, so when Windows introduced its User Account Control dialog in Windows Vista – a desultory attempt to block malware through a confirmation prompt that requires you to simply click Yes or OK to any process’s attempt to gain carte blanche access to your system – many Linux users sat back and smirked.
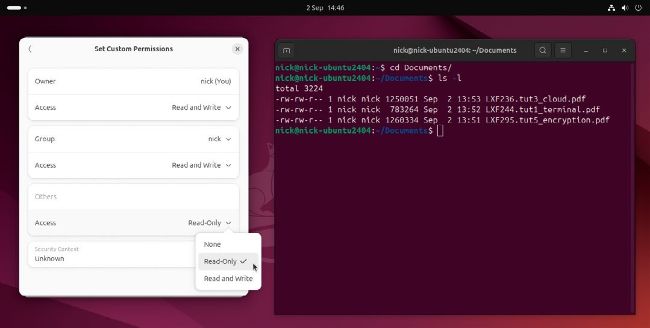
You can view a file’s permissions using both your file manager (left) and the ‘ls -l’ command in the terminal (right).
Even now, the Windows UAC dialog fails to mask its underlying insecurity, where everyone is given admin levels of access by default. In contrast, Linux applies a strict user privilege model whereby even administrator-level users don’t have full access to the system. Instead, the highest level of access is restricted to a single root user (also known as superuser). Administrators can gain temporary access to the root user one of two ways. First, when you’re logged on to your desktop and you – or the system – attempts to perform a task that requires superuser levels of access, you see a prompt requiring you to enter your user password. Once entered, your user gains temporary root access to the system for the purposes of performing that specific task only.
QUICK TIP
Password security good practice involves changing your passwords on a regular basis – including the one you use to log into Linux. Set yourself an alarm to change this every six months – visit Settings > System > Users to do so in Ubuntu.
HARDWARE SECURITY
The Linux filesystem is designed to allow Linux to treat everything as a file – even hardware devices.
Type sudo lshw and press Enter, and you’re given a long list of all the internal and external hardware devices connected to your PC.