Hacker’s toolkit 2022
Nmap deep dive
Nmap, the stealthy port scanner, is a vital tool for any helpful hacker or nefarious network administrator’s arsenal.
W
e’ve seen how the humble ping command can tell us not just if our machines are reachable, but how many of them are on the local network. If we read into the timings column a bit, we might even speculate about how far away these machines are. However, for network reconnaissance and port scanning, you can’t beat Nmap.
Since we’ve already got an XML list of machines on our LAN it would be nice if we could re-use it here to save scanning again. Sadly, the XML files generated by Nmapsi4’s network discovery can’t be easily digested by Nmap itself (or we couldn’t figure out a way). So let’s open a terminal and do it manually. To start, just enter the following:
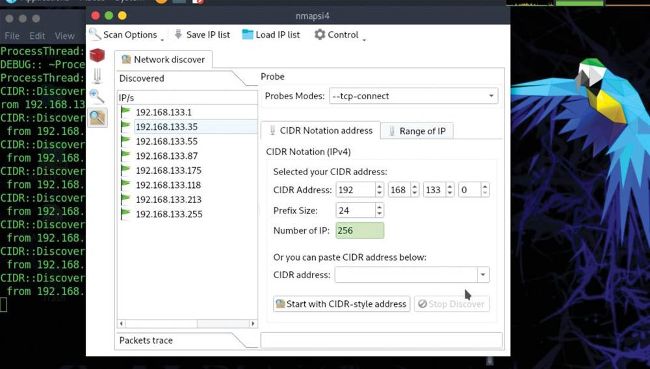
Once you’ve discovered your network click Scan Options to commence more thorough script scanning of the machines.
NORTHERN EXPOSURE
The Common Vulnerabilities and Exposures (CVE) database is a fantastic dataset operated by The Mitre Corporation at the behest of the US government. It tracks vulnerabilities as they’re discovered and cross-references them with the internal tracking systems of companies and distros, so it’s easy to determine which versions or which releases are vulnerable.
In addition to CVE, there’s the associated National Vulnerabilites Database (https://nvd.nist.gov), where CVEs are rated by severity. Several of the CVE numbers related to the ShellShock vulnerability score a perfect 10. As do other CVEs that affect popular software, allow remote code execution and can be carried out by fools (script kiddies). ‘Person in the middle’ attacks, which might be hard to pull off in the real world and only lead to user impersonation or limited information leakage, might score more modestly. Besides CVE entries, you can also search the Common Platform Enumerations (CPE) database, which makes it easy to find vulnerabilities in a particular product.
Sooner or later someone will release Proof of Concept (PoC) code showing how to exploit a particular vulnerability. Ideally, this happens after the issue is responsibly disclosed to the affected vendors or projects, giving them time to ship patches. If not, it’s a race between cyber fiends attacking and security teams patching.