EBPF Credit: www.ebpf.io
Monitor your TCP/IP networks with eBPF
Naturally suspicious, Mihalis Tsoukalos keeps an eye on all his network traffic using eBPF – and he’ll show you how, too.
OUR EXPERT
Mihalis Tsoukalos is a systems engineer and a technical writer. He is the author of Go Systems Programming and Mastering Go, 3rd edition.
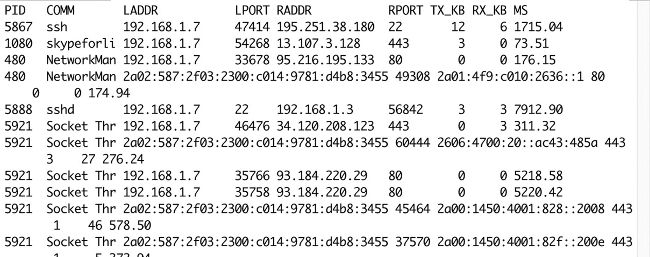
This is the kind of output generated by the TCPlife utility, which traces the lifespan of TCP sessions.
S ure to send a shiver down the nerdiest of geek’s spines, the idea of monitoring TCP/IP S packets and connections can be confusing at best. Just scan this article and the output of the eBPF tools, and you realise you need to be familiar with TCP/ IP and its cryptic options in order to understand the provided information. Before diving into the TCP/IP tools, we’ll begin by explaining how to trace eBPF related system calls with the help of the Strace utility.
Let’s use Strace to trace eBPF-related system calls along with their parameters. For example, we can find out the eBPF system calls executed with Opensnoop:
This is a small part of the generated output but you get the idea and the insights of the system calls related to eBPF. Using filtering tools such as Grep can help you locate what you are looking for because Strace produces lots of output.
What we see here is three versions of the BPF system call. The first one using the BPF_MAP_CREATE command, the second one using BPF_MAP_UPDATE_ELEM and the last one using BPF_RAW_TRACEPOINT_OPEN . In LXF297, we discussed eBPF maps and how each map has a file descriptor associated with it – this can be seen in action here: the first call creates a map and returns a file descriptor with a value of 4, whereas the second statement uses 4 as its map_fd parameter in order to update the desired map.
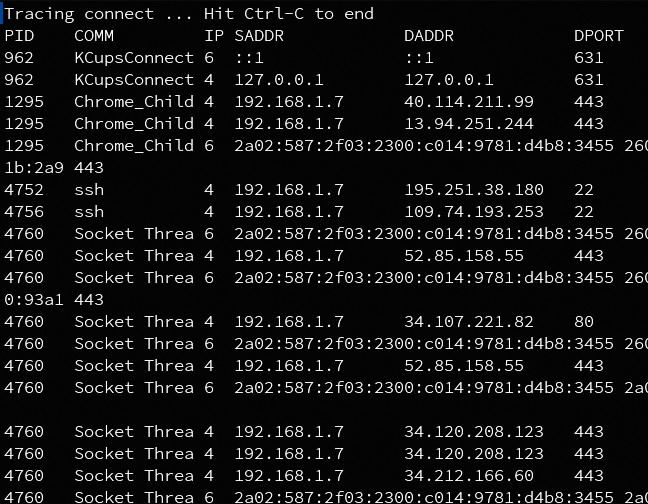
Here you can see the output from the TCPconnect utility, which traces TCP connect calls.
Traditional TCP/IP tools
Before deciding to use eBPF utilities, consider using one of the existing Unix ones. The list of such tools includes butis not limited to the following:
• Netstat: Shows information about the network
status of a Unix machine. It’s a powerful tool that can
work on the Socket, TCP, UDP, IP and Ethernet levels.
Its main drawback is that it only works on the local
machine but doesn’t usually need root to operate.